PAHARIS AND PADDARIS
1. Context
2. Who are the Scheduled Tribes?
- The Constitution of India under Article 366(25) defines Scheduled Tribes as "such tribes or tribal communities or parts of or groups within such tribes or tribal communities as are deemed under Article 342 to be Scheduled Tribes.
- Article 342 empowers the President of India to specify, through a public notification, the tribes or tribal communities to be included in the list of Scheduled Tribes for each state or union territory.
Once a tribe or tribal community is recognized as Scheduled Tribe, it is entitled to certain benefits and protections, including:
- Reservation in educational institutions: STs receive reserved seats in government and private educational institutions to improve their access to quality education.
- Reservation in government jobs: STs are provided with reservations in public sector employment to ensure fair representation and opportunities.
- Socio-economic development schemes: Various government programs and schemes are implemented to uplift the living standards of Scheduled Tribes, addressing issues related to healthcare, housing, infrastructure, and livelihood.
- Land rights and protection: The government safeguards the land and forest rights of STs, especially in tribal-dominated areas, to preserve their traditional way of life.
- Constitutional safeguards: Special provisions in the Constitution safeguard the cultural, social, and political rights of STs.
The list of Scheduled Tribes is specific to each state or union territory in India, and it may vary from one region to another based on historical, cultural, and geographical factors. The Central and State governments continuously review and update the list to include new communities and exclude those that have progressed socio-economically and no longer require the special status.
3. ST Communities in Jammu & Kashmir
- Paharis in Jammu and Kashmir comprises Hindus, Muslims, and Sikhs, including Kashmiris who settled in Rajouri and Poonch districts over time.
- The J&K government recommended including Paharis in the ST list in 1989, but it was rejected due to no record of their caste/tribe.
- To address Paharis' demands for ST status, an Advisory Board for Development of Pahari Speaking People was set up, defining them as people living in Rajouri and Poonch, except those already listed as STs.
- Various governments tried to grant ST status to Paharis, but it faced multiple rejections from the Centre, citing a lack of ethnic categorization.
- In 2019, under Governor Satya Pal Malik, Paharis were given 4% reservation in jobs and education.
- In 2022, the Justice (retd) G D Sharma Commission recommended ST status for Paharis, along with Gadda Brahmins, Kolis, and Paddari Tribe. The proposal was approved by the Registrar General.
4. Status of STs in India
- The Census 2011 has revealed that there are said to be 705 ethnic groups notified as Scheduled Tribes (STs).
- Over 10 crore Indians are notified as STs, of which 1.04 crore live in urban areas.
- The STs constitute 8.6% of the population and 11.3% of the rural population.
5. Pahari Tribe
- The Paharis tribe is a diverse ethnic group in the Jammu and Kashmir region of India. They are found in the districts of Rajouri and Poonch, with members belonging to various religious backgrounds, including Hindus, Muslims, and Sikhs.
- The Paharis also include people of Kashmiri origin who migrated and settled in these areas over time. The Paharis have historically faced socio-economic challenges and educational backwardness.
- In response to popular demand from the Paharis residing in the border areas of Rajouri and Poonch, who argued that they shared similar social and educational disadvantages as the Gujjars, Bakerwals, Gaddis, and Sippis (Scheduled Tribes of the region), the Jammu and Kashmir government set up an Advisory Board for the Development of Pahari Speaking People.
- Efforts to grant the Paharis Scheduled Tribe (ST) status have a long history. In 1989, the J&K government recommended their inclusion in the ST list, but it was initially rejected by the Registrar General of India due to the absence of the Pahari caste/tribe in official records.
- Over the years, several proposals and recommendations were made to provide reservation benefits to the Paharis, but they faced challenges related to ethnic categorization and official approvals.
- Finally, in 2019, under the tenure of Governor Satya Pal Malik, the Paharis were granted 4% reservation in government jobs and admission to educational institutions.
- Additionally, the Justice (retd) G D Sharma Commission, appointed in the same year, recommended ST status for the Pahari Ethnic Group, along with Gadda Brahmins, Kolis, and the Paddari Tribe. This proposal was approved by the Registrar General in 2022.
- Despite their diverse religious and cultural backgrounds, the Paharis share a common identity based on their historical settlement in the Rajouri and Poonch regions.
- The recognition of the Pahari Ethnic Group as a Scheduled Tribe has provided them with greater opportunities for socio-economic development and representation in various sectors.
6. Paddari Tribe
- The Paddari Tribe, also known as the Pahari Paddari, is an ethnic group residing in the Jammu and Kashmir region of India.
- They are primarily found in the districts of Rajouri and Poonch, which are part of the Pir Panjal mountain range. The Paddari people have a distinct cultural heritage and a unique way of life.
- The Paddari Tribe is primarily involved in agriculture, animal husbandry, and pastoral activities. They are known for rearing livestock, especially cattle, goats, and sheep.
- The tribe's livelihood is closely tied to their animals, and they migrate with their herds to higher altitudes during summers and return to lower regions before the onset of winter. This nomadic lifestyle is similar to that of the Gujjars and Bakerwals, who are also prominent ethnic groups in the same region.
- Historically, the Paddari Tribe has faced socio-economic challenges, including educational backwardness and limited access to basic amenities. As a result, they have been seeking official recognition and benefits through Scheduled Tribe (ST) status.
- In 2019, the Justice (retd) G D Sharma Commission, appointed by the Jammu and Kashmir government, recommended ST status for the Paddari Tribe along with the Pahari Ethnic Group, Gadda Brahmins, and Kolis. The Registrar General approved this proposal in 2022, granting the Paddari Tribe the much-awaited ST status.
- With the inclusion in the ST list, the Paddari Tribe is entitled to various reservation benefits, including access to government jobs, educational institutions, and social welfare schemes aimed at promoting their socio-economic development. This recognition also provides them with enhanced representation and voice in matters concerning their community.
- Overall, the Paddari Tribe holds a significant cultural identity in the region and plays an important role in the local economy through its traditional practices of animal husbandry and agriculture.
- The official recognition of their tribal status is expected to contribute to their overall well-being and foster socio-economic progress within their community.
|
For Prelims: Pahari Tribe, Paddari Tribe, Scheduled Tribe, Constitution (Jammu and Kashmir) Scheduled Tribes Order (Amendment) Bill, 2023, Article 366(25), and Article 342.
For Mains: 1. Analyse the challenges and opportunities faced by Scheduled Tribes in India with regard to socio-economic development, education, and representation in governance. (250 words).
2. What are the two major legal initiatives by the state since Independence addressing discrimination against Scheduled Tribes(STs)? (UPSC 2017)
|
Previous year Questions1. Under which Schedule of the Constitution of India can the transfer of tribal land to private parties for mining be declared null and void? ( UPSC 2019)
(a) Third Schedule
(b) Fifth Schedule
(c) Ninth Schedule
(d) Twelfth Schedule
Answer: b
2. If a particular area is brought under the Fifth Schedule of the Constitution of India, which one of the following statements best reflects the consequence of it? (UPSC 2022)
(a) This would prevent the transfer of land of tribal people to non-tribal people.
(b) This would create a local self-governing body in that area.
(c) This would convert that area into a Union Territory.
(d) The State having such areas would be declared a Special Category State.
Answer: a
|
LOW EARTH ORBIT (LEO)
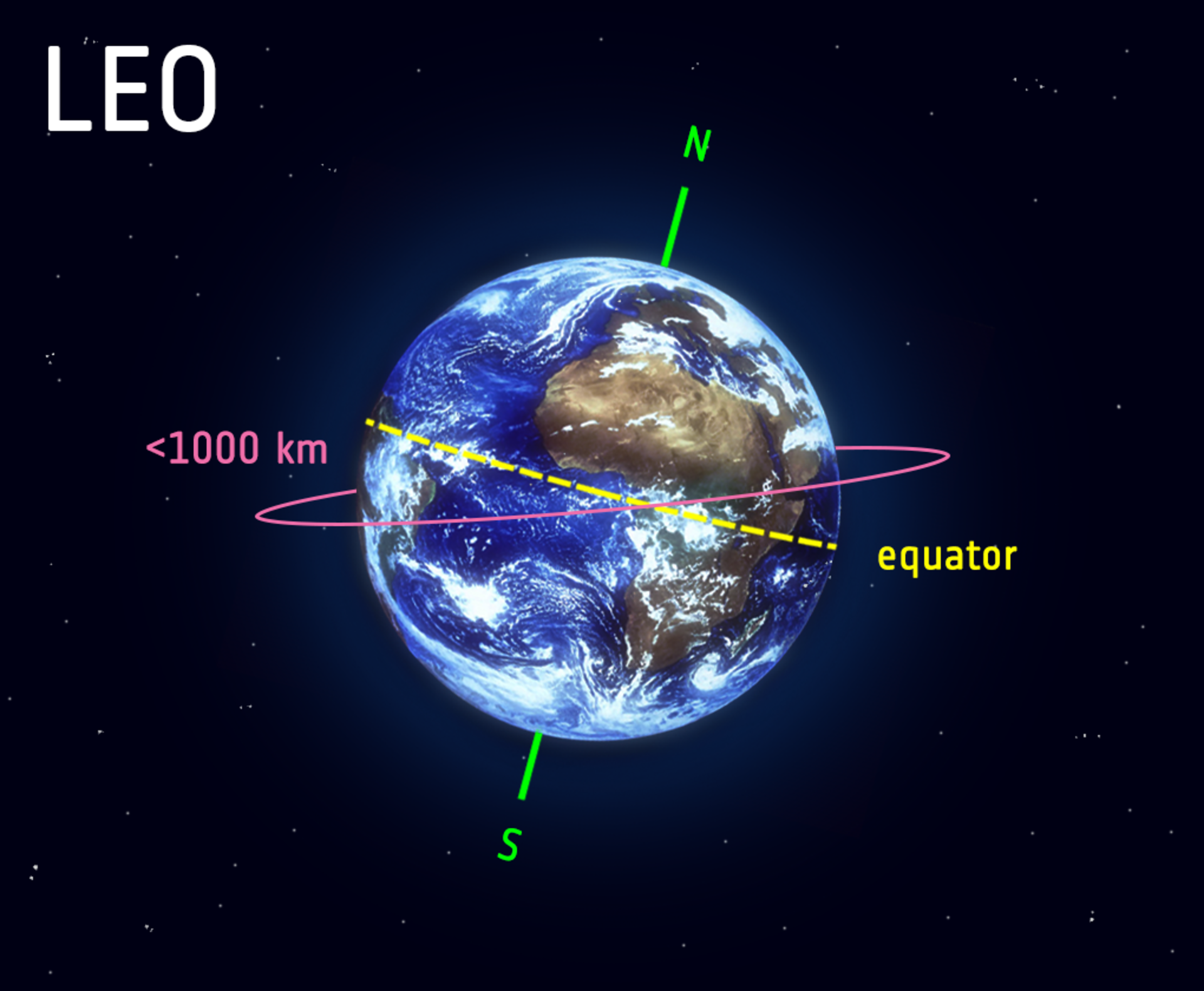
Low Earth Orbit (LEO) is an orbit around Earth with an altitude of 2,000 kilometers (1,200 miles) or less. It is the most common type of orbit for artificial satellites, and it is used for a variety of purposes, including:
- Earth observation: LEO satellites can provide high-resolution images of the Earth's surface, which can be used for a variety of purposes, such as monitoring environmental change, tracking weather patterns, and providing military intelligence.
- Communication: LEO satellites can be used to relay communications signals between different parts of the Earth. This is especially useful in remote areas that are not served by terrestrial communications infrastructure.
- Navigation: LEO satellites are used by the Global Positioning System (GPS) to provide accurate positioning information to users on the ground.
- Scientific research: LEO satellites can be used to conduct a variety of scientific experiments, such as studying the Earth's atmosphere, the Sun, and the stars.
- Shorter orbital periods: Satellites in LEO have shorter orbital periods than satellites in higher orbits. This means that they can transmit data to Earth more quickly.
- Lower communication latency: The lower orbital period of LEO satellites also means that there is lower communication latency, which is the time it takes for a signal to travel from the satellite to Earth.
- Closer to Earth: LEO satellites are closer to Earth than satellites in higher orbits. This means that they can be serviced more easily, and they are less likely to be affected by space debris.
DS-SAR stands for Dual-Speed Synthetic Aperture Radar. It is a Singaporean SAR Earth Observation satellite that was launched into orbit on July 30, 2023.
The satellite was developed and built by Israel Aerospace Industries (IAI) for the Defence Science and Technology Agency (DSTA) of Singapore.
DS-SAR is a dual-frequency SAR satellite, meaning that it can operate at two different radar frequencies: C-band and L-band.
This allows the satellite to produce images with different characteristics, depending on the frequency used. For example, C-band images are typically better at resolving fine details, while L-band images are better at penetrating clouds and other obscurants.
6.Polar Satellite Launch Vehicle (PSLV)
The Polar Satellite Launch Vehicle (PSLV) is an expendable launch vehicle developed and operated by the Indian Space Research Organisation (ISRO).
It is a three-stage, solid-and-liquid-fueled rocket that is capable of launching satellites into Low Earth Orbit (LEO), Sun-synchronous orbits, and Geosynchronous Transfer Orbit (GTO)
The PSLV has been used to launch a wide variety of satellites, including Earth observation satellites, communication satellites, and scientific satellites.
It has also been used to launch commercial satellites for customers around the world
7.Geosynchronous Satellite Launch Vehicle (GSLV)
The GSLV is an expendable launch vehicle developed and operated by the Indian Space Research Organisation (ISRO).
It is a three-stage, liquid-fueled rocket that is capable of launching satellites into geosynchronous transfer orbit (GTO)
The GSLV was first launched in 2001, and has since been used to launch a variety of satellites, including communication satellites, weather satellites, and scientific satellites
|
For Prelims: Low Earth Orbit (LEO), PSLV, GSLV
For Mains: 1.Discuss the significance of the Polar Satellite Launch Vehicle (PSLV) in India's space program. Highlight its features and capabilities that have made it a reliable and preferred launch vehicle for both domestic and international satellite missions
2.GSLV (Geosynchronous Satellite Launch Vehicle) is a crucial component of India's space endeavors. Elaborate on its design, stages, and payload capacity. Compare and contrast GSLV with PSLV in terms of their applications and advantages
|
|
Previous Year Questions
1.A low earth orbit satellite can provide large signal strength at an earth station because: (ESE Electronics 2011)
A. Path loss is low
B. These orbits are immune to noise
C. Large solar power can be generated at these orbits
D. Lower microwave frequencies in s-band can be used
Answer-A
|
KURIL ISLANDS
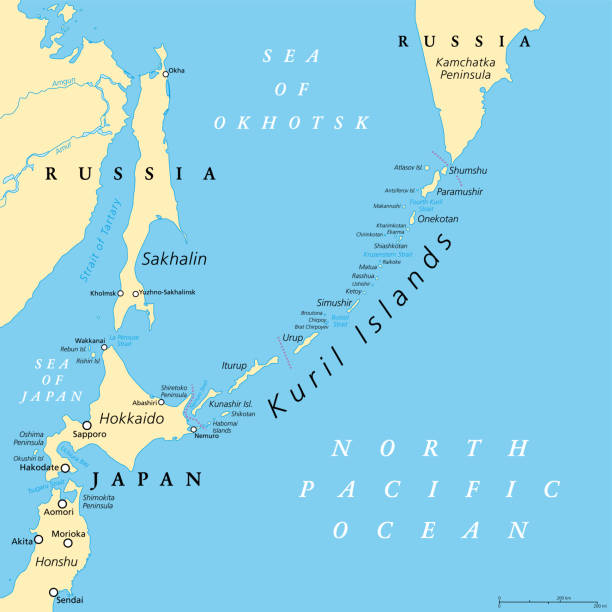
- Throughout history, the Kuril Islands have been subject to territorial disputes between Japan and Russia.
- The disagreement stems from the aftermath of World War II when the Soviet Union took control of the islands, which were previously part of Japan's territory.
- The dispute over the islands' ownership remains unresolved to this day, with both countries claiming sovereignty over the southernmost four islands of the chain: Iturup, Kunashir, Shikotan, and Habomai.
- Moscow and Tokyo have held talks about the Iturup (Etorofu in Japanese), Kunashir (Kunashiri), Shikotan and Habomai Islets several times in the past, but failed to agree on a solution.
- This led to the two sides never formally signing a peace treaty to end the war
- China is not a direct party to the dispute, but it has expressed support for Russia's claim to the islands. In 2022, China and Russia conducted a joint military exercise on the Kuril Islands, which was seen as a sign of support for Russia's position
- There are a number of reasons why China might support Russia's claim to the Kuril Islands. First, the islands are strategically important, as they control access to the Sea of Okhotsk. Second, China may see the dispute as a way to weaken Japan, which is a US ally.
- Third, China may be trying to curry favor with Russia, as it seeks to counter US influence in the region
- China and Russia do share a border, and like with any neighboring countries, they may have other geopolitical issues and interests that they need to address.
- However, as of my last update, the Kuril Islands dispute remains a matter primarily between Japan and Russia
|
For Prelims: Kuril Islands, World War II, World War I
For Mains: 1.The Kuril Islands and Russia's Far East Policy: Evaluate the role of the Kuril Islands in Russia's foreign and domestic policies, particularly in terms of resource exploration, economic development, and maintaining territorial integrity.
2.Geopolitical Interests in the Kuril Islands: Examine the involvement of other countries or international organizations in the Kuril Islands dispute and their interests in the region. Discuss the significance of the Kuril Islands in global geopolitics
|
|
Previous Year Questions
1.The Kuril Island dispute or Northern Territories dispute, is a dispute between Japan and ------ (UPRVUNL AE ME 2014)
A. China
B. South Korea
C. Russia
D. Philippines
Answer-C
|
AKIRA RANSOMWARE
1. Context
2. Akira Ransomware
- The Akira ransomware is designed to encrypt data, create a ransomware note and delete Windows Shadow Volume copies on affected devices.
- The ransomware gets its name due to its ability to modify filenames of all encrypted files by appending them with the “.akira” extension.
- In recent times, the Akira ransomware has emerged as a serious cyber threat, targeting corporate networks across various domains, including education, finance, real estate, manufacturing, and consulting.
- This ransomware is specifically designed to encrypt data, leaving victims helpless unless they pay a ransom to the attackers.
- Using VPN services, it tricks users into downloading malicious files. After infecting a device, it steals sensitive data and extorts victims for a ransom.
- Organizations should maintain offline backups, update systems regularly, use strong passwords, and implement multi-factor authentication to protect against Akira ransomware.
.png)
Akira ransomware employs various techniques to infiltrate and compromise devices:
- Infection Methods: The primary method of infection is through spear-phishing emails that contain malicious attachments in the form of archived content (zip/rar) files. Additionally, the ransomware may spread via drive-by downloads, which inadvertently download malicious code onto the victim's device, or through specially crafted web links in emails that lead to the download of malicious code. It has also been observed to exploit insecure Remote Desktop connections.
- Encryption and Deletion: Once the ransomware infects a device, it proceeds to encrypt the victim's data, appending the ".akira" extension to all encrypted files. The malware is also designed to delete Windows Shadow Volume copies, rendering recovery through traditional means nearly impossible.
- Service Termination: Akira ransomware terminates active Windows services using the Windows Restart Manager API to prevent interference with the encryption process.
- Targeted Encryption: To maintain system stability, the ransomware avoids encrypting certain critical folders like Program Data, Recycle Bin, Boot, System Volume Information, and key Windows system files with specific extensions (e.g., .syn, .msl, and .exe).
- Extortion and Communication: Once the data is encrypted, the ransomware leaves behind a note named "akira_readme.txt," containing information about the attack and a link to the Akira gang's negotiation site on the dark web. Victims are given unique negotiation passwords to communicate with the attackers via a chat system on the site.
To safeguard against Akira ransomware and other similar threats, users, and organizations can implement the following security measures:
- Maintain Offline Backups: Regularly back up critical data to offline storage to ensure data recovery in case of a ransomware attack.
- Keep Systems Updated: Ensure that operating systems and networks are regularly updated with the latest patches and security fixes. For legacy systems, consider using virtual patching.
- Implement Email Security: Enforce Domain-based Message Authentication, Reporting, and Conformance (DMARC), DomainKeys Identified Mail (DKIM), and Sender Policy Framework (SPF) to prevent email spoofing and spam.
- Use Strong Passwords and MFA: Enforce strong password policies and implement multi-factor authentication (MFA) to add an extra layer of security to user accounts.
- Restrict External Devices: Adopt a strict external device usage policy to prevent unauthorized access and potential malware introduction.
- Encrypt Data in Transit and at Rest: Implement data-at-rest and data-in-transit encryption to protect sensitive information from unauthorized access.
- Block Potentially Malicious Attachments: Configure email systems to block attachment file types that are commonly associated with malware (e.g., .exe, .pif, .url).
- Conduct Regular Security Audits: Perform periodic security audits of critical networks and systems, especially database servers, to identify vulnerabilities and weaknesses.
5. Computer Emergency Response Team (CERT)
- Computer Emergency Response Team (CERT) is a specialized group of experts responsible for providing rapid response and support during cyber security incidents.
- CERTs play a crucial role in detecting, analyzing, and mitigating cyber threats and vulnerabilities.
- These teams are often established within organizations, government agencies, or independent entities, and their primary objective is to enhance overall cybersecurity readiness and incident response capabilities.
6. Key Functions of CERT :
- Incident Handling and Response: CERTs are equipped to handle various cybersecurity incidents, such as malware infections, data breaches, ransomware attacks, and denial-of-service (DoS) attacks. They investigate the incidents, assess the impact, and take necessary actions to contain and mitigate the threat.
- Threat Intelligence and Analysis: CERTs continuously monitor and analyze emerging cyber threats, vulnerabilities, and attack patterns. They collect threat intelligence to better understand the evolving threat landscape and develop proactive defense strategies.
- Information Sharing: CERTs facilitate the sharing of cybersecurity information and best practices among stakeholders, including other CERT teams, organizations, government agencies, and private sectors. This collaboration helps in improving the collective defense against cyber threats.
- Vulnerability Management: CERTs assist in identifying and addressing vulnerabilities in software, systems, and networks. They work closely with vendors and developers to coordinate the responsible disclosure and timely patching of security flaws.
- Cybersecurity Awareness and Training: CERTs promote cybersecurity awareness among employees, users, and the general public. They conduct training sessions and awareness campaigns to educate individuals about safe online practices and potential threats.
- Proactive Measures: CERTs conduct risk assessments, penetration testing, and security audits to proactively identify weaknesses in an organization's security posture. They recommend and implement measures to strengthen overall cybersecurity resilience.
- Incident Coordination: In the case of large-scale cyber incidents that affect multiple organizations or sectors, CERTs play a critical role in coordinating response efforts, ensuring effective communication, and facilitating collaboration among relevant parties.
- CERTs operate based on established frameworks and guidelines, such as those defined by the Forum of Incident Response and Security Teams (FIRST) and the United States Computer Emergency Readiness Team (US-CERT).
- They often collaborate with law enforcement agencies, regulatory bodies, and international cybersecurity organizations to address global cyber threats.
|
For Prelims: Akira Ransomware, Forum of Incident Response and Security Teams (FIRST), the United States Computer Emergency Readiness Team (US-CERT), Multi-factor authentication (MFA), Domain-based Message Authentication, Reporting, and Conformance (DMARC), DomainKeys Identified Mail (DKIM), and Sender Policy Framework (SPF)
For Mains: 1. Examine the spread and impact of Akira ransomware on corporate networks across various domains. Discuss the methods employed by the attackers to infect devices, especially focusing on the role of spear-phishing emails, drive-by downloads, and insecure Remote Desktop connections. (250 words).
|
|
Previous year Questions
1. The terms 'WannaCry, Petya, and EternalBlue' sometimes mentioned in the news recently are related to (UPSC 2018)
A. Exoplanets
B. Cryptocurrency
C. Cyberattacks
D. Mini satellites
Answer: C
|
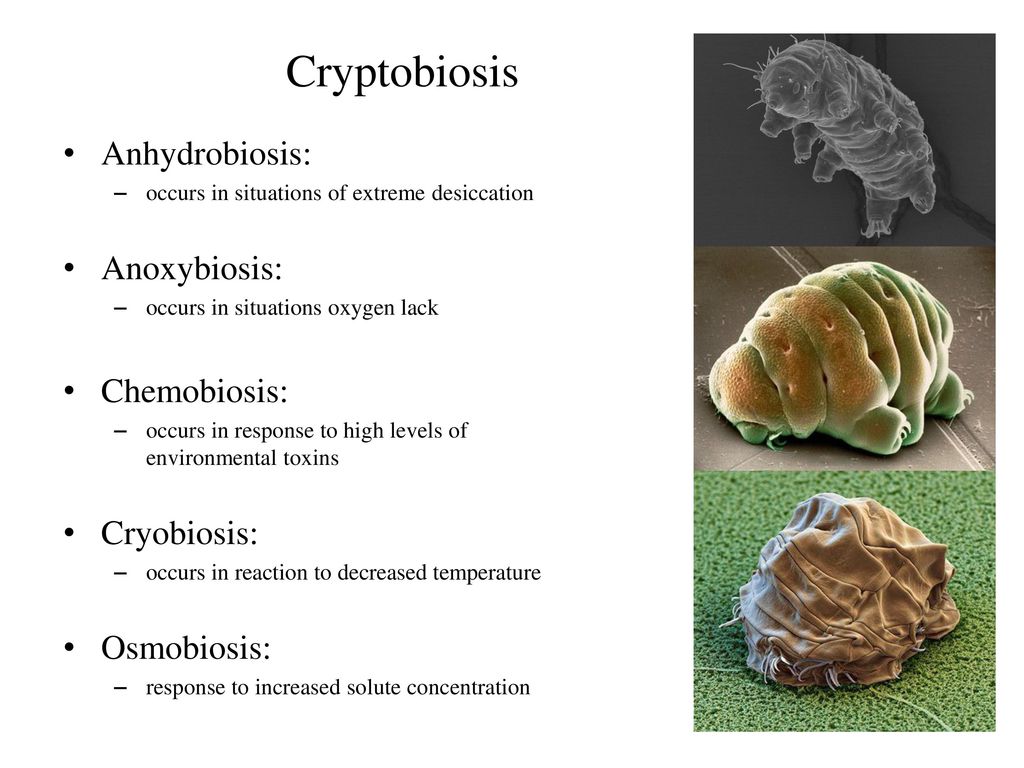
CRYPTOBIOSIS
- Cryptobiosis is a state of extreme inactivity in response to adverse environmental conditions. In the cryptobiotic state, all metabolic processes stop, preventing reproduction, development, and repair.
- In cryptobiosis, an organism can live almost indefinitely while it waits for environmental conditions to become better
- Cryptobiosis is a biological state or condition in which an organism enters a state of suspended animation, where its metabolic processes almost completely halt, allowing it to withstand extreme environmental conditions that would otherwise be lethal.
- This term is commonly associated with certain microorganisms, invertebrates, and even some plant seeds that can survive in harsh environments, such as extreme temperatures, high radiation, desiccation (extreme dehydration), and lack of oxygen
- Many animals like nematodes, and more famously, tardigrades, can survive extreme conditions by entering a dormant state called “cryptobiosis.”
There are several types of cryptobiosis, the most common include:
- Anhydrobiosis (lack of water): This is the most common type of cryptobiosis. Organisms that can enter anhydrobiosis are able to survive by reducing their water content to very low levels. This is typically done by producing special proteins that help to protect the cells from damage. Examples of organisms that can enter anhydrobiosis include tardigrades, nematodes, and brine shrimp.
- Cryobiosis (low temperature): Some organisms are able to survive freezing temperatures by entering a state of cryptobiosis. In this state, the water in the cells of the organism is converted to ice, but the cells themselves do not freeze. This is because the organism produces special proteins that prevent the formation of large ice crystals, which can damage the cells. Examples of organisms that can enter cryobiosis include tardigrades, lobsters, and some insects.
- Osmobiosis (increased solute concentration): Some organisms are able to survive in environments with high solute concentrations, such as salt water. They do this by entering a state of cryptobiosis in which the cells of the organism are able to tolerate the high solute concentration. Examples of organisms that can enter osmobiosis include brine shrimp and some bacteria.
- Anoxibiosis: Some organisms can survive without oxygen for prolonged periods, like certain bacteria and rotifers.